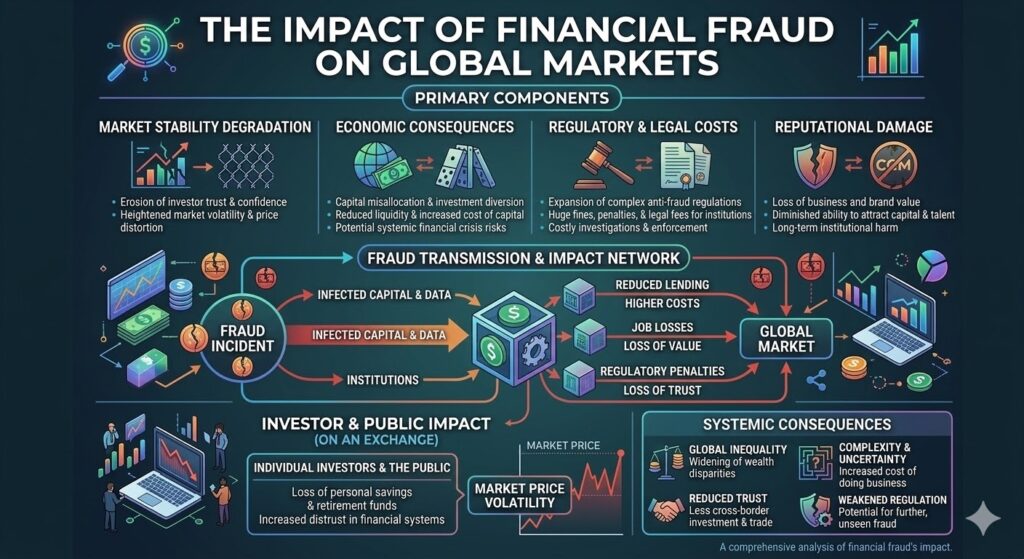
The Impact of Financial Fraud on Global Markets: A 2026 Perspective
In the interconnected landscape of 2026, the global financial system operates at a speed once unimaginable. Digital transactions are near-instantaneous, and artificial intelligence (AI) manages everything from high-frequency trading to personal wealth. However, this evolution has brought a shadow: financial fraud. No longer confined to simple “phishing” emails, modern financial crime is a sophisticated, multi-billion-dollar industry that threatens the very stability of global markets. Understanding the impact of financial fraud is no longer just a concern for compliance officers; it is a critical macroeconomic issue. As of 2026, the costs are not merely financial—they are systemic, eroding trust and distorting market efficiency. The Massive Scale of the Fraud Crisis Recent data from early 2026 indicates that global fraud losses in financial services have continued their steep upward trajectory. Estimates suggest that total global losses related to scams and fraudulent activities reached approximately $450 billion in the past year alone. This










